Data and Cyber Security
Foxcomm provides organisations and businesses the tools and a digital landscape to protect and secure trade, commerce and business information. We specialise in supplying the best in-class IT security solutions to many financial, law and media firms all over the globe.
Protect What Matters
IT and data security are critically important for businesses, regardless of their size or industry. With the increasing amount of sensitive and confidential data being generated and stored by businesses, the risk of cyber attacks and data breaches has become a major concern. Here are some reasons why IT and data security are crucial for businesses:
1. Protection of sensitive data: Businesses handle a large amount of sensitive data, such as customer information, financial data, intellectual property, and employee records. If this data falls into the wrong hands, it can lead to financial losses, reputational damage, and legal liability. IT and data security measures help to protect this data from unauthorized access, theft, and misuse.
2. Compliance with regulations: Businesses are subject to a growing number of regulations and laws related to data privacy and security, such as GDPR and HIPAA. Compliance with these regulations is mandatory, and failure to do so can result in severe penalties and legal consequences. IT and data security measures help businesses to comply with these regulations and avoid costly violations.
3. Prevention of cyber attacks: Cyber attacks are a growing threat to businesses of all sizes and types. Attackers can use a variety of methods to gain access to business networks and data, including malware, phishing, and social engineering. IT and data security measures help businesses to detect and prevent these attacks, and mitigate their impact if they do occur.
4. Preservation of business reputation: A data breach or cyber attack can damage a business’s reputation and erode customer trust. This can have long-lasting effects on the business’s brand and bottom line. IT and data security measures help businesses to avoid these negative outcomes by ensuring that sensitive data is protected, and that any incidents are handled quickly and transparently.
5. Continuity of business operations: IT and data security are also important for ensuring the continuity of business operations. A cyber attack or data breach can disrupt business operations, causing downtime, lost revenue, and productivity. IT and data security measures help to minimize these disruptions, ensuring that businesses can continue to operate even in the face of unexpected events.
Overall, IT and data security are critical for businesses that want to protect their data, comply with regulations, prevent cyber attacks, preserve their reputation, and ensure the continuity of their operations. By investing in robust IT and data security measures, businesses can better protect themselves from the growing threats in today’s digital landscape.
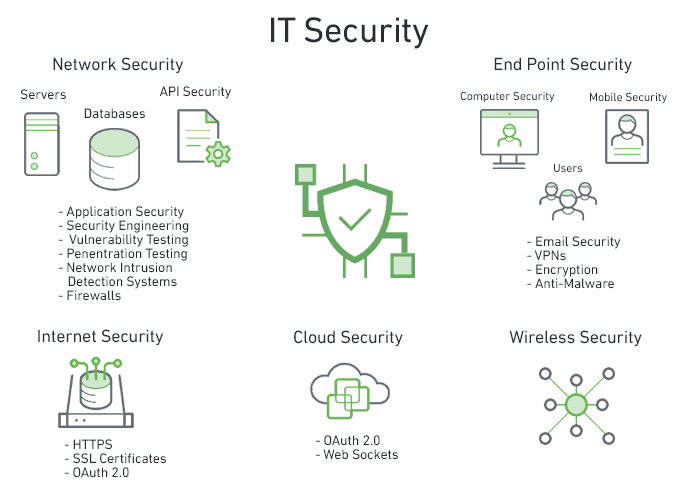
Foxcomm deploys various types of IT and data security measures that businesses can implement to protect their sensitive information and networks. Here are some common types of IT and data security measures:
1. Firewalls: Firewalls like Sonicwall are hardware or software based devices that act as a barrier between a business’s internal network and external networks such as the internet. Firewalls can be configured to block unauthorized access to the network and can help to prevent cyber attacks and data breaches.
2. Antivirus software: Antivirus software is designed to protect devices from malware such as viruses, worms, and Trojans. Antivirus software can detect and remove malicious code, preventing it from infecting a business’s network.
3. Data encryption: Encryption is the process of converting data into a code that can only be read with a key or password. Encrypted data is difficult to access without authorization, which can help to protect sensitive data from unauthorized access.
4. Access controls: Access controls can help businesses to limit access to sensitive information by requiring users to provide credentials such as usernames and passwords. Access controls can also be used to restrict access to certain areas of a network or to certain functions.
5. Intrusion detection systems (IDS): IDS are designed to monitor network traffic for suspicious activity and can help to identify and prevent cyber attacks. IDS can also provide alerts when potential threats are detected, allowing businesses to respond quickly and effectively.
6. Vulnerability scanners: Vulnerability scanners are tools that can help businesses to identify vulnerabilities in their networks and applications. By identifying vulnerabilities, businesses can take steps to address them and reduce the risk of cyber attacks.
7. Security policies and training: Businesses can also implement security policies and training programs to educate employees on the importance of IT and data security, as well as best practices for protecting sensitive information. This can include training on password management, phishing scams, and other security risks.
These are just a few examples of the types of IT and data security measures that foxcomm can implement to protect their networks and sensitive information. By taking a comprehensive approach to IT and data security, businesses can better protect themselves from the growing threats in today’s digital landscape.

